With the number of dedicated email filter solutions available on the market, it only makes sense to disable or remove any other network burden that will hinder the traffic of email. A boarder gateway firewall is normally not the location to have an email filter deployed on your network. As a default, Cisco PIX does have the option for email filtering. Although it is not as sophisticated as some other third party filters, it is there when you need it. You can normally notice this option being enabled when performing simple troubleshooting steps such as attempting to telnet to an email server. If you are not presented with a server banner or greeting but rather the following, then there is a good chance that the PIX MailGuard is enabled:

To have the MailGuard feature disabled on the PIX, you will need to login to the console and follow the steps below.
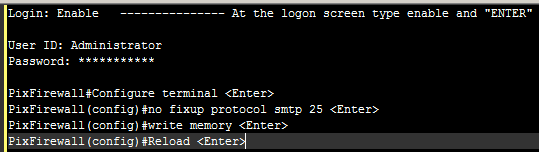
With the changes done above, email flow through your firewall should not be hindered by the PIX email filter and it will prevent any other issues while making troubleshooting more efficient.



