NOTE: If you’re running modus on Windows 2008 or Windows 2012, this does not apply to you
The SHA family of hashing algorithms was developed by the National Institute of Standards and Technology (NIST) and is used by the majority of SSL certificates. Presently, the most common of these hashing algorithms is SHA1 which was adopted by certificate authorities as the successor of MD5 algorithm because it signified a major advancement in cryptographic security. Over the years computing power has strengthened and SHA1 level of encryption has been considered as not being sufficiently secure. As a result there has been a major advancement to transition from SHA1 to the stronger SHA2 algorithm. The recent announcement from Microsoft and Google about deprecating support for SHA1 in browsers has accelerated this transition. There are, however, a few systems that continue to operate using SHA1. This includes most servers running Windows 2003 (not R2). Users who continue to operate using SHA1-based security certificates can expect to receive security warnings from web browsers by the end of this month (October).
As of January 1st 2017, support for SHA1 will completely come to an end and it is highly likely that updates will be sent out to all major platforms to start erroring out on SHA1 requests.
“Microsoft’s SHA-1 deprecation plan differs in the activation time and browser behavior. Microsoft’s security advisory on “Deprecation of SHA-1 Hashing Algorithm for Microsoft Root Certificate Program” informed us that Windows will cease accepting SHA-1 SSL certificates on January 1, 2017. To continue to work with Microsoft platforms, all SHA-1 SSL certificates issued before or after this announcement must be replaced with a SHA-2 equivalent by January 1, 2017. The SHA-1 deprecation plans also impact SHA-1 intermediate certificates; SHA-2 end-entity certificates must be chained to SHA-2 intermediate certificates to avoid the adverse browser behaviors described above. SHA-1 root certificates are not impacted.” — From Symantec’s website.
The problem with this is that an unpatched Vanilla Windows 2003 server does not support SHA2 natively. Even a patched Windows 2003 does not support SHA1. To be able to support SHA2 you need to be running Windows 2003 R2 SP2 fully patched.
“Windows users do not need to do anything in response to this new technical requirement – Windows XP Service Pack 3 supports SHA2 SSL certificates, and Windows Server 2003 Service Pack 2 or later add SHA2 functionality to SSL certificate by application of hotfixes (KB968730 and KB938397).”
In other words, if you’re running Windows 2003R2 SP2 or better with the related hotfixes, you should be fine. However you should verify your current certificates to confirm if they are encoded using SHA1 versus SHA2.
If you’re not patched, you really should start updating your Windows 2003R2 with the latest service packs & security fixes. According to GlobalSign, to support SHA2 (SHA 256) with Windows 2003, you need Windows 2003 R2 SP2 + MS13-095 (KB2868626). More here.
KB2868626 should already be installed if your server is going through the normal windows updates process.
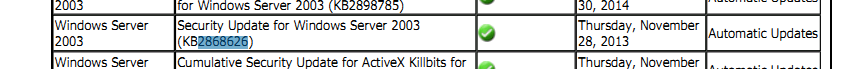
https://support.microsoft.com/en-us/kb/2868626
%MCEPASTEBIN%
What does all of this mean for you?
For modus users running Windows 2003 “Vanilla”:
As of November 1st 2015, any user hitting your web server over https will get certificate warnings. For example Google Chrome will indicate that the site is “secured but with issues”.
Furthermore, you may experience issues related to your ability to receive spam and virus updates may be delayed since they go through https. Towards the end of October our team will provide you with host entries that you will be able to put into your Windows host file to redirect the update requests to these servers, so you can continue receiving spam and virus updates without any problems while using SHA1.
It is strongly advised that you migrate off of Windows 2003 as soon as possible. The operating system itself is not supported by Microsoft at this point and Vircom is discontinuing support for Windows 2003 completely starting with Version 6.1 of modusGate and modusMail.
Vircom can assist you with your migration to new servers. We have a vast amount of experience with this and if you do not wish to move to a new server and a new OS, we can also move you to our cloud spam filtering service as an alternative (for those running modusGate).
Windows 2003 R2 SP2 (fully patched)
Clients using Windows 2003 R2 SP2 with all the updates will not be affected by these changes. Our testing indicates that modus has no issues in getting updates from SHA2-based update servers.
However, if you offer https access to your webMail or webQuarantine and the certificate being used is SHA1, your users will get security warnings. If you switch to a SHA2 certificate, that should fix the issue.
Windows 2003 is still EOL so we strongly recommend that you migrate to Windows 2008 or 2012. With the release of modus 6.1, Windows 2003 will NO LONGER be supported. If you need help our support team is here to assist you.
The list of servers to put in your host file will be provided towards the end of October.
Please contact our support team should you have any other questions.
Sincerely,




Leave a Comment