Fortify your Email Gateway:
Stop BEC Attacks with
Vircom’s Solutions
Protect your Business from
Costly BEC Attacks with Vircom
What is Business Email Compromise (BEC)?
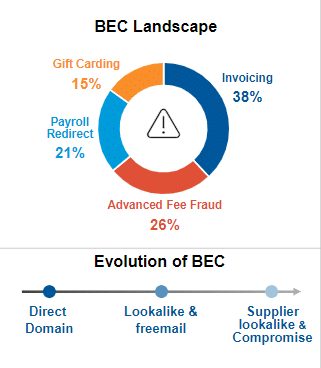
Types of Business Email Compromise (BEC) Scenarios
Classic BEC Scenarios
CEO Fraud
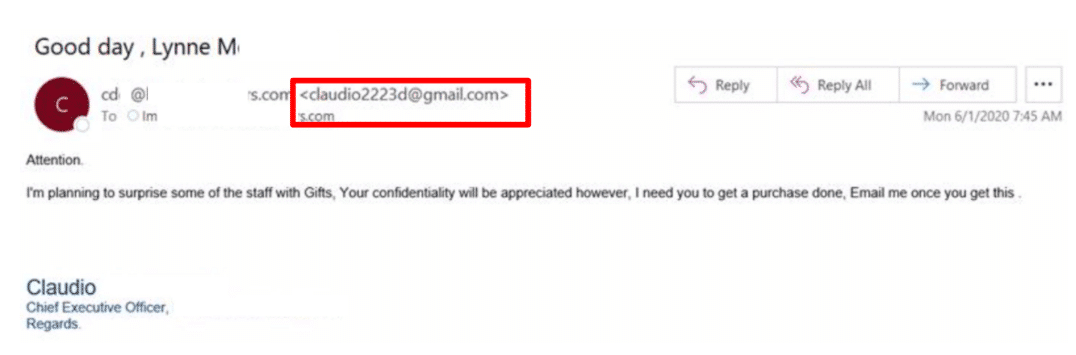
In CEO fraud, cybercriminals pose as top executives to demand urgent wire transfers via fake emails. The success of CEO Fraud is rooted in its element of surprise, urgency, and the authority the 'CEO' wields, often bypassing standard verification protocols for transactions. Attackers use 'Masquerading' to create emails that closely resemble the CEO’s, using similar addresses and well-researched information to appear authentic.
Vendor Email Compromise
This scam involves a compromised email from a trusted supplier, where the hacker requests a bank account update for future payments. When the recipient updates the account, payments are redirected to the scammer. Vendor Email Compromise is hard to prevent as it often occurs within ongoing conversations, making verification of payment changes difficult. The single most important thing that organizations can do in their ransomware prevention strategy is to ensure that they have good backups.
Email Account Compromise (EAC)
Simpler than other BEC scenarios, account compromise EAC, includes phishing, social engineering, or malware to access an individual's email within an organization. Attackers monitor email activity, payment workflows, and launch more phishing attacks to escalate BEC operations, potentially leading to fraudulent transfers, invoice manipulation, and data harvesting for future scams or sale on the dark web.
Examples of Business Email Compromise (BEC)
2022
2019
2023
Understanding BEC Scams and Attacks Risks
CEO Fraud
Financial Loss: Cybercriminals deceive employees into transferring funds under false pretenses.
Vendor Email Compromise
Reputational Damage: Trust in the organization may be eroded due to involvement in fraudulent activities.
Invoice Manipulation
Data Breaches: Sensitive financial information may be compromised, leading to potential regulatory violations.
Employee Impersonation
Business Disruption: Operations may be disrupted if key employees are targeted, and their accounts compromised.
Lawyer Impersonation
Legal Liability: Legal ramifications may arise if sensitive legal documents are compromised.
How to Prevent Business Email Compromise (BEC)
Implementing these preventive measures can significantly reduce the risk of falling victim to (BEC) Business Email Compromise scams and protect your organization’s assets and data from harm.
BEC Email Security Measures
and Best Practices
Implement robust business email compromise protection and protocols to prevent unauthorized access.
Business Email Compromise Detection
Educate employees on recognizing common signs of BEC scams to detect and prevent fraud.
Business Email Compromise
Phishing Protection
Enhance BEC phishing protection measures to block suspicious emails and prevent data breaches.
BEC Security Solutions and Strategies
Invest in comprehensive security solutions and training programs to mitigate BEC risks.
ROBUST PROTECTION BUNDLES
Protect your business
with Vircom's comprehensive security bundles.
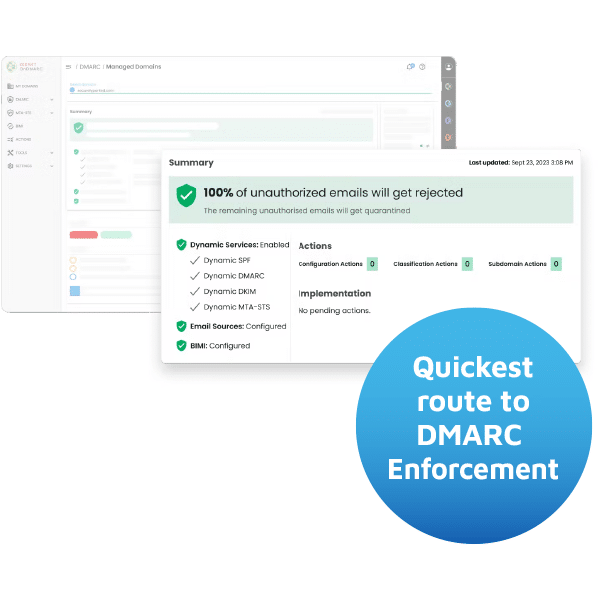
DMARC, DKIM and SPF
A Closer Look into Vendor Email Compromise (VEC) and Its Implications
Vendor Email Compromise (VEC) is a specialized form of BEC that targets vendors and suppliers within a business ecosystem. Cybercriminals exploit vulnerabilities in vendor communication channels to intercept payment requests or alter banking information, leading to fraudulent transactions and financial losses.
Implications of VEC include:
Financial Losses
Unauthorized changes to vendor payment details can result in substantial financial losses for both the targeted organization and its vendors.
Reputational Damage
VEC incidents can erode trust between businesses and their vendors, damaging reputation and potentially leading to the loss of valuable partnerships.
Regulatory Compliance Risks
Failure to adequately protect against VEC attacks may expose organizations to regulatory fines and legal consequences for non-compliance with data protection laws.
Comprehensive BEC Protection with Vircom
Protect Against BEC and EAC
Vircom extends its protection to cover both Business Email Compromise (BEC) and Email Account Compromise (EAC), ensuring a comprehensive defense against all forms of email fraud. By safeguarding against unauthorized access to email accounts, Vircom protects your business from the inside out.
A Trusted Partner in BEC Defense
Vircom’s dedicated BEC protection solutions offer a robust line of defense against these insidious attacks, combining technology, education, and real-time monitoring to secure your email communications. With Vircom solutions, you can protect your business from BEC scams, ensuring the integrity of your email systems and the continuity of your business operations.
Strengthen your defenses with Vircom’s comprehensive Business Email Compromise protection.

