I’m assuming you already know what SPF (Sender Policy Framework) is and know how it is important enough for you to set it up properly. If you don’t, then I suggest you read this article on the basics of the SPF record. Properly setup SPF records can protect your domain from email spoofing.
Step 1 – Identify all the places sending email on your behalf
Internal Systems:
• Any mail server(s) you may be running that will be sending mail from yourdomain.com.
• Any anti-spam gateways that might also be sending emails out on your behalf including bounce notifications.
• Any webpage or website with a small MTA (Message Transfer Agent) that might be sending mail on your behalf.
• Don’t forget any alerting/monitoring systems that could be sending mail from alerts@yourdomain.com for instance.
Note down the public IPs these systems will be sending out Emails on your behalf.
External Systems:
• Most companies now outsource many of their operations, like for instance CRMs (example: Microsoft Dynamics, SalesForce, etc ..). That means these systems will also very likely be sending Email on your company’s behalf. Usually they will already have an SPF declared for their MTAs so all you need to do is “include” their SPF record into your SPF record. It’s best to check with the particular services help desk or knowledge base as some companies can have a separate SPF record for their internal corporate Email and the MTAs used to send mail on behalf of for their clients.
Once you’ve identified which public IPs and which services your company is using that could be sending Email on your behalf, you need to configure an SPF record for your domain.
For the sake of this article, we’ll use the following. Our hypothetical company (ModusStuff Inc) with the domain of modusstuff.com has three servers, and they use the services of Constant Contact (to send monthly newsletters to their clients).
Mail Server 1 – 101.10.10.20
Mail Server 2 – 101.10.10.21
Spam Gateway – 67.96.24.10
Constant Contact’s SPF is bound to constantcontact.com
Note that it is very important that you identify ALL systems that might be sending mail on your domains’ behalf before you implement an SPF record otherwise mail servers on the internet that receive email for your domain will start bouncing email or sending messages to their spam quarantine.
Step 2a – Configuring your DNS server (we’re assuming you’re using it to control external resolutions)
We will use Microsoft DNS for this example.
First, go into your domain zone
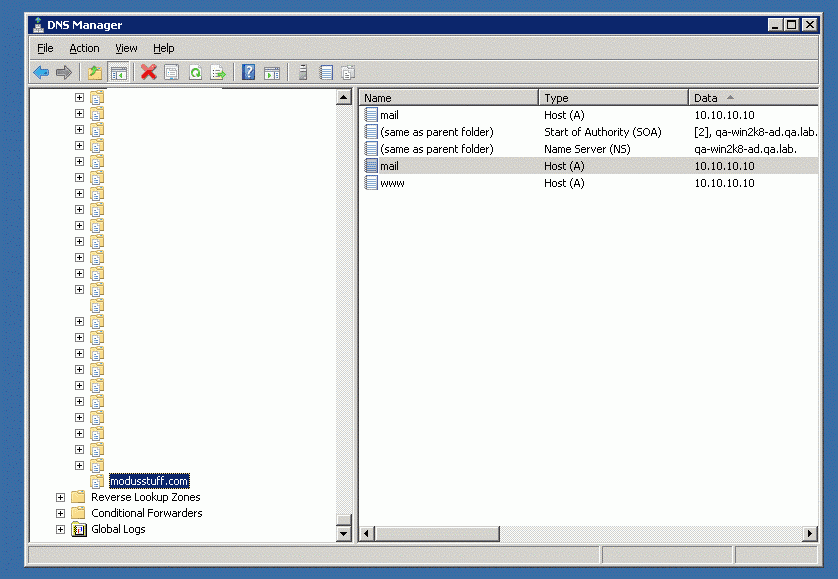
Create a new TXT record for the domain (in this case modusstuff.com)
Right-click on the domain zone you want to edit.
Click on “Other New Record”.
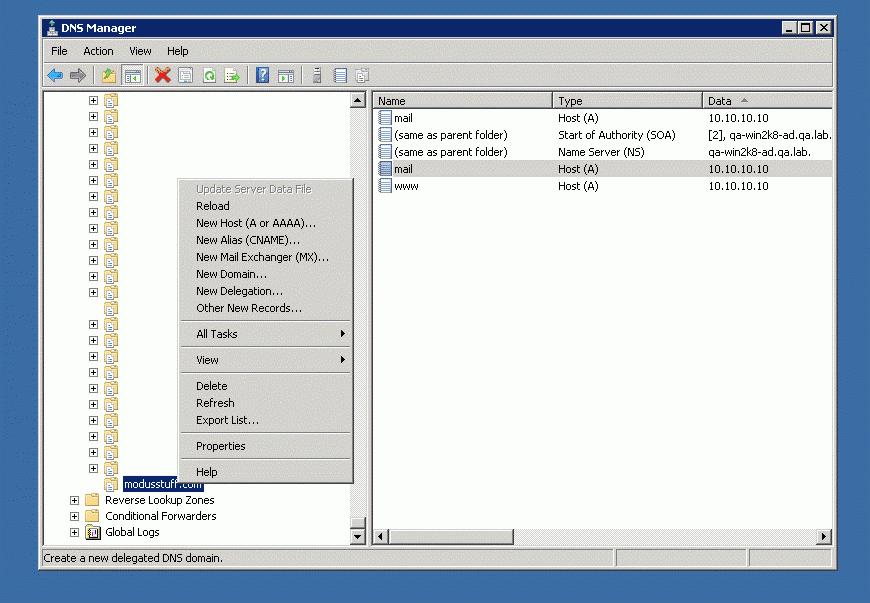
Using the scroll bar, scroll down to TEXT (TXT) and click “CREATE RECORD”
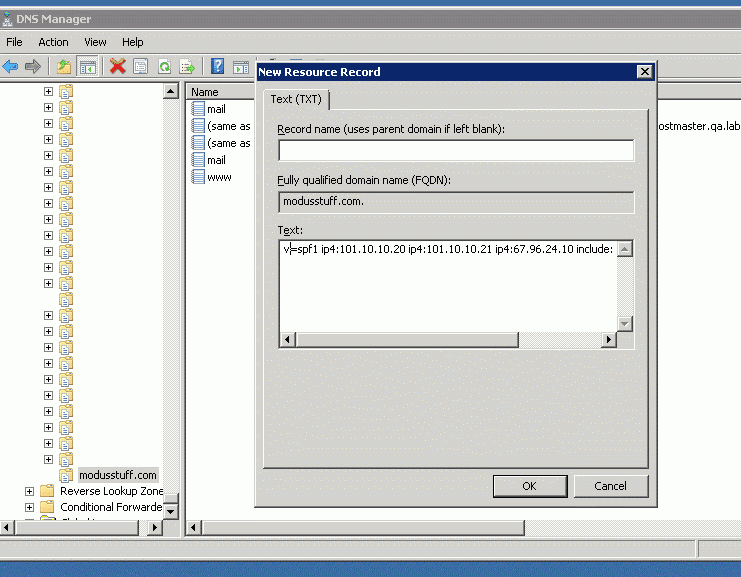
In the TEXT part, paste in your SPF string you created and click OK.
V=spf1 ip4:101.10.10.20 ip4:101.10.10.21 ip4:67.96.24.10 include:constantcontact.com -all
This should be the result:
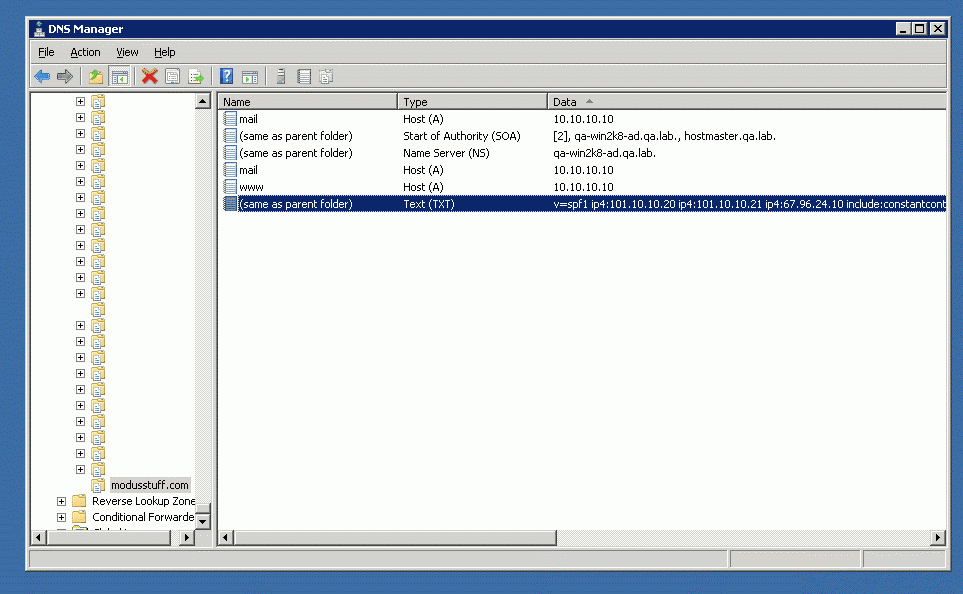
Note that “-all” at the end of the line.
“-all” means a hard fail. You are recommending to mail servers on the internet to interpret the SPF record as a hard fail, usually meaning to reject messages that don’t come from your authorized IP addresses.
If you change it to “~all”, that’s a soft-fail. Most MTA/Filters on the internet will ascribe a spam score to a failed SPF check and will increase the spamminess of messages coming from unauthorized IP.
We recommend using a soft fail first to see how things go and then change later on to a hard fail.
Step 2b – Configuring using a web-based DNS service (in this example, DYNDNS)
Note that most web-based DNS Services differ so this is just an example.
Login to your account with your web-based DNS service
Go to the location where you manage your DNS Zone service
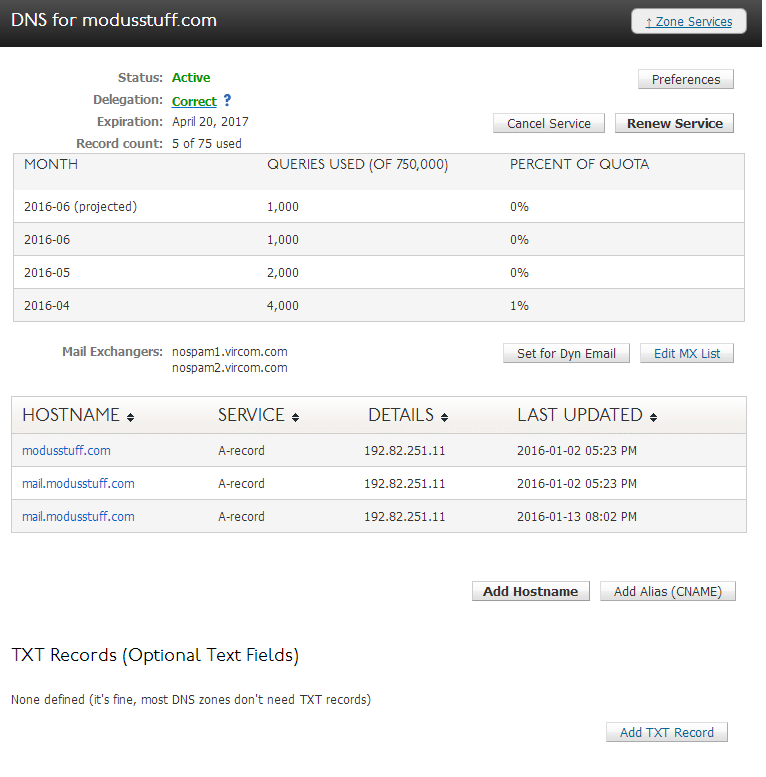
Click on the “ADD TXT Record at the bottom”
In the TXT record, we basically put this in:
V=spf1 ip4:101.10.10.20 ip4:101.10.10.21 ip4:67.96.24.10 include:constantcontact.com -all
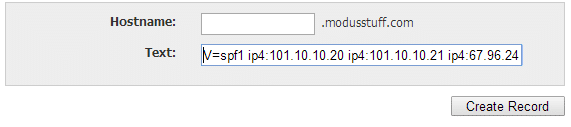
Click on Create Record.
Here’s the result:
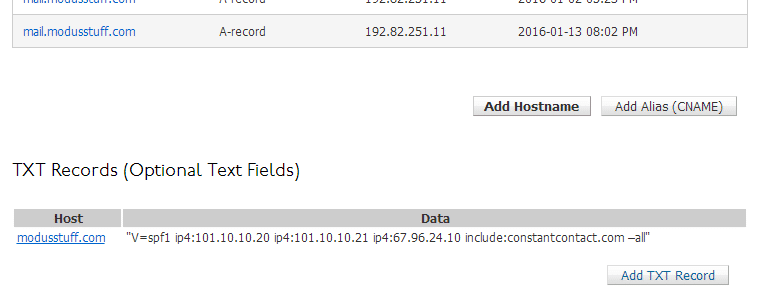
Step 3 – Make sure the changes took effect.
Note that it can take a few hours for the changes to propagate.
Open a DOS prompt
Type: ipconfig /flushdns
This clears your local DNS cache.
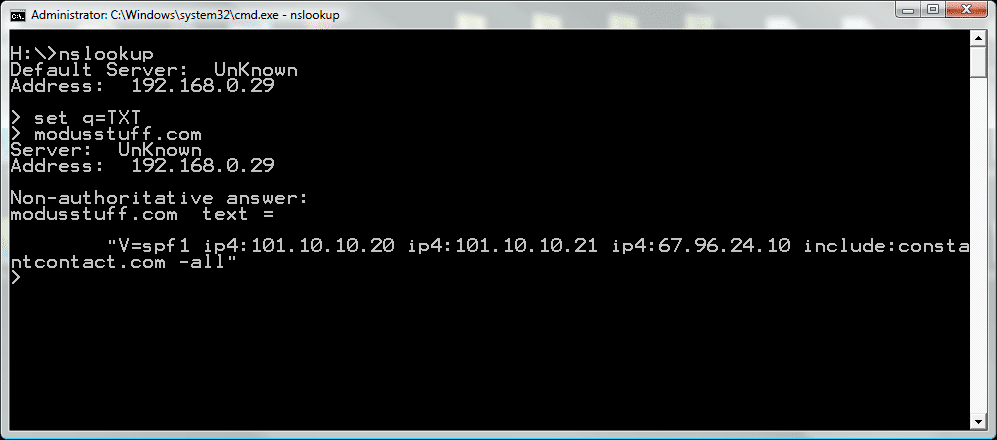
Type: nslookup – 8.8.4.4 <enter>
This will lookup using google’s DNS servers. It’s usually better to check using an external DNS than using your own internal DNS that might have a different result. Google’s DNS is a good reference server.
Type: set query=TXT
Type: modusstuff.com
The result should look like this:
If it doesn’t, either the change hasn’t taken effect yet, you didn’t commit the change in your DNS server or something else happened.
Conclusion
Contact us if you’d like help. We love helping IT admins set up SPF and find that too many either avoid doing it at all or set it up improperly.
Remember, a properly set up SPF record will help ensure that spammers won’t use your domain name to pretend to send email on your behalf. They will not spoof you.



