Someone is spoofing your email address. They are pretending to be you (email spoofing) in the hopes of phishing unsuspecting users and distributing malware to them. You are receiving complaints from people in companies you have never heard of, telling you to stop sending them viruses, malware and spam. Angry admins are asking you to beef up your security settings.
You probably have a million questions going on in your head when this happens. Panic is often a normal part of the reaction. Calm is best though, as most spoofing cases aren’t because your account has been hacked. Let’s clarify the difference between “hacked/compromised” and “infected” as it pertains to someone spoofing your email address.
Hacked: Your real email account has been compromised. A malevolent third party has full access to your account. They somehow successfully retrieved your password, gained access to your systems beyond your email, possibly took over an open web session, etc. They can send emails from your account so traffic will look legitimate and technically be legitimate by all normal criteria of authenticity.
Infected: You (or one of your friends, colleagues, contacts) has been infected by malware and your email history and/or address book (or theirs) has been stolen. The criminals send emails that seem to be on your behalf but not directly from your email account. This is where the actual spoof comes along, as they have to disguise the email since they cannot send directly from your real account as would be the case if you had been hacked.
Most spoofing occurrences are due to an infected machine somewhere on your network or on one of your contact’s networks. These occurrences do not use your credentials to log into your account and send spam, they are only using your name and contact names to spoof your email address, using mail servers controlled for this pernicious purpose. If a hacker has your credentials, they can do a lot worse than just spoof your email and you’ve got bigger things to worry about.
Business spoofing
Businesses exchange emails with thousands of recipients. They often use generic email addresses such as support@domain or sales@domain, along with a formatted signature and detailed contact information. One fine day, a colleague or a customer somewhere on the planet clicks on a malicious attachment, promising fortune or a health miracle, and is infected. This infection is like a tiny virtual spy that sifts through that user’s email history and contacts, using advanced algorithms to steal precious information. At this point the criminals will know the following about you:
- Your full name
- Your email address
- Whom you communicate with
- What form your emails take when making such communications, down to your signature details
All this information comes in very handy when they begin to pretend to be you by spoofing your email address. Here’s a reasonably well-done sample.
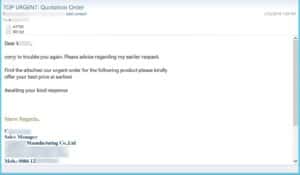
This is when you might start sweating. The body text of the email is exactly the same as an email that you routinely send. While the FROM email address is far from being similar to the original one, the content is. The “stolen” signature is identical to the original one (including color and font). The message is urgent and usually requires immediate attention. It is key to inject a level of urgency to make the recipient act quickly without thinking. The attached file has a familiar name, the same name as a recent file attachment received from this account. The user that clicks will get infected by opening the file. Should they be suspicious and use the Reply-To email to respond, someone is listening on the other end and will respond that everything is ok.
And if your signature has an image embedded or a quote from someone famous? No problem! It only makes the copy created and used that much more reliable to the recipient and more capable of fooling them.
Here’s another example:
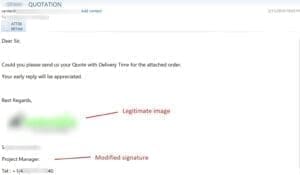
The legitimate image was extracted from the infected user’s email history. The contact information is very similar compared to the original legitimate email that was copied and is meant to only be glanced at to reassure you. But this one contains a modified signature. The phone number does not actually work, so you cannot call and confirm the request. The original attachment was “Quotation.iso”, a file installer, that has been removed by the email filter.
Votre entreprise opère en français et vous vous croyez à l’abri? Non, pas du tout. [Translation: You operate in a language other than English, for example, French, and you think you might be protected? Think again!]
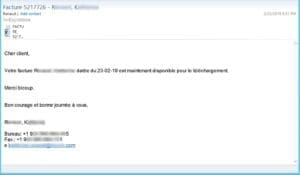
We have seen a huge uptick in French and Spanish spoofs. In this case, the sender and recipient know each other, increasing the risk for the recipient to be fooled by the fake. The copied content re-uses a mistake that the original sender had made (“bicoup” should be “beaucoup”). The spoofed email is even copying style.
How can I fix this?
In most cases of spoofing you have not been hacked. There is however an infection somewhere and it is probably off-site, i.e. not on your network. The spamming criminal can be using a random server anywhere on the planet to send emails, so there is not much you can do to act directly on the email exchange. There are a few things you can do to help legitimate mail servers and mail filtering tools worldwide make better decisions on whether email purported to be sent by you was actually sent by you. This is done by publishing properly formatted SPF, DKIM and DMARC records.
SPF (Sender Policy Framework) would be the minimum. This is probably the most under-used email security feature of all. SPF informs email recipients from what IP ranges legitimate emails from your business will come. While this helps, it is not a miracle solution. If for example you are using Office 365 SPF, a spammer on Office 365 with a valid SPF record could pass the test even though they would be impersonating you. A well-configured email security solution will always check the SPF record of the domain from which it has received an email and will reject emails sent from the wrong server.
DKIM (DomainKeys Identified Mail) is a bit more complex but very effective. It adds a (hidden) signature to your email to prove that your business actually sent it. The authenticity is established using encryption and asymmetric keys. Many email providers support DKIM.
DMARC (Domain Message Authentication Reporting and Conformance) is more complex, the larger the business the more complex it will be to implement. It combines the best of SPF and DKIM. DMARC allows a domain to publish whether it uses SPF and/or DKIM, and what to do with an email received from that domain that fails either test. While DMARC could be an excellent tool to protect against phishing, its adoption by the market has been underwhelming because of the high False Positives rates. The main reason for the False Positives is incorrectly set up records that result in rejection of what are for all intents and purposes legitimate emails. We’ve written before about it here.
Conclusion
Spammers and scammers are going to extraordinary lengths to fool those that know you by sending emails pretending to be from you (spoofing). The cause of this is often a minor infection that didn’t even happen on your own network. You can protect yourself, your business and your reputation by adopting more advanced standards and protocols for your business email such as SPF, DKIM and DMARC.
Another thing you can do is use an advanced and complete email security solution that is backed by security experts whose pleasure it will be to set up your SPF, DKIM and DMARC correctly.
Other References on SPF, DKIM and DMARC.
Photo by Greg Ortega on Unsplash



