On March 1st 2018, Alabama became the last state to require that businesses notify their customers when their data has been breached (within 45 days of its occurence). Only a few days before that, South Dakota’s State Senate made it second-to-last in passing Bill No. 62, unanimously requiring breach notifications to customers and the attorney general’s office (also within 45 days).
While the establishment of data breach notification laws and their ratification across the United States has come through a long and winding road, now that it is nearly complete (South Dakota’s law has not been signed into law), the landscape of different data breach requirements that exist across the country is complicated and fragmented. While federal data breach disclosures have not been required across all businesses and industries by the US government to the level of GDPR for organizations operating in the EU, there are still broad implications for US businesses in state-by-state disclosure requirements. At the very least, all states have breach notification laws to be aware of.
Here are a few of them and how they vary depending differing state regulation.
The Information Covered by Breach Notification Law:
For an incident to be considered a data breach, all states require the incident to include the loss of, at minimum, a first name or first initial and last name, along with any of:
- A Social Security number,
- A driver’s license number
- A state issued ID,
- Private banking related information.
Personal information would not include what would be generally considered publicly available. These are the very basics. On a state-by-state level, information such as passwords with login names, taxpayer ID numbers, medical information, passport numbers, biometric data and others can all be enough to require data breach notifications. Those are further elaborated in the helpful data breach chart produced by Baker Law.
Notice Requirement to Attorney General or State Agencies:
The lowest threshold for Attorney General or State Agency notification of a data breach is Indiana, at 250 state resident records. For other states, this threshold (where there is one) generally starts at 500 or 1000 residents’ records breached.
It is important to read a state-by-state description of process. In many states, notifying the Attorney General is required before reaching out to affected users.
Was Harm Done:
If, after an analysis of the impact of the breach, it is determined that no harm was done, most states don’t require notification. The Harm Standard is a tricky one, and the onus is on the breached company to prove that the data breach will not result in harm to those affected. Still, in several states, like California and Texas, companies are required to notify affected parties. Note that it is also unclear if you are required to notify the regulatory body or attorney general before or after conducting the analysis.
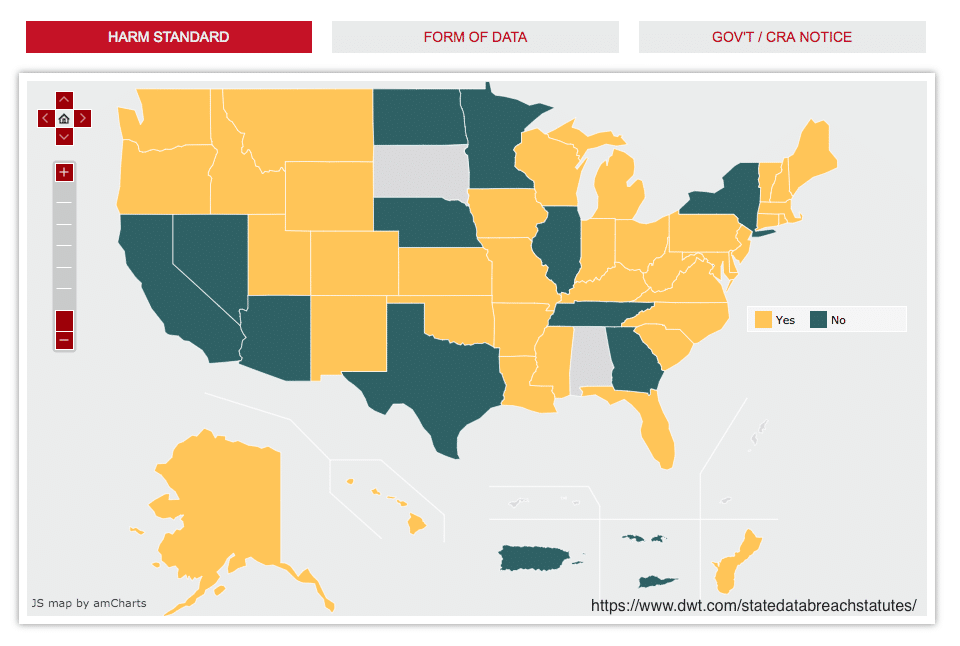
Length in Reporting to Customers or Regulatory Bodies:
Across the board, reporting is required in the most expedient time possible. Public agencies in Idaho have 24 hours to inform the Attorney General on becoming aware of a breach. Otherwise, reporting lengths appear to be similar to those of customers. In terms of maximums for those impacted, the range is generally between 30-90 days maximum, with a median of around 45. That is of course – those that have them. Otherwise, the default is to expediency and without unreasonable delay. These laws also generally have a disclaimer that they need to be consistent with law enforcement needs (for example, reporting to customers can or should be delayed in cases where it would impact an ongoing investigation).
Customer Notice Format:
Generally, variable forms of written, telephone or email notifications are required to customers often with eSign in digital cases, for authenticity. Some states, such as New York, require tangible physical notice unless the customer has elected to receive the notice electronically (with records being kept). If by telephone, some states require proof that the customer was contacted successfully.
Other Interesting State by State Differences Include:
- It seems roughly 20 states will allow for private legal action if data breach notification rules are violated. These range from a maximum of $5000 in damages in North Carolina to Oregon, where the state can act rather than private civil action being taken.
- From what we gather, if your customer records are encrypted (and the hacker did not obtain a key) you are protected from these breach data notification regulations. In California, Delaware, and Iowa among others, there’s an added stipulation that if it’s possible that the key has been obtained, the safe harbor no longer applies.
- How you inform regulatory bodies can vary on a state-by-state basis, ranging from mail to online forms to even a fax. The information requested varies as well.
It can be confusing to say the least, and the last thing a company wants to deal with is a liability risk of this size, but addressing data breaches promptly is the first step to rectifying any damage they can cause. It may also give some respite from any legal nightmares, in which 40 states (and a couple territories) have their own unique protocols.
The point of all this, however, is not to give legal advice – we are not lawyers after all. First and foremost, the above should make the heavy cost of a data breach clear, well beyond the notification requirements a breach entails. While the lead source for data breaches is usually either human error or email or… both at once, preventive measures should be taken to hedge against this risk.
The second point is that a more comprehensive approach to regulating not only data breach disclosure but also cyber security measures and responses across the board (even at the federal level) would streamline enforcement and perhaps reduce the confusion or misreporting faced by the likes of Equifax and Uber. With GDPR coming into effect Across the EU, and Canada likely adopting PIPEDA in the Spring of 2018, the US is rapidly falling behind on this front.
Until more comprehensive federal policies are introduced, your best bet is to implement a stronger awareness and training program, make sure you are using leading email and cyber security technology, encrypting data in transmission and, if all else may fail, keep a good lawyer on retainer.
[highlight_sc bg_color=#21c2f8 text_color=#ffffff border_color=]More Resources:[/highlight_sc]
A Visual Summary of U.S. State Data Breach Notification Statutes.
Great summary table of GDPR compared to US regulation by IAPP.
A State-By-State Data Breach Chart Courtesy of Baker Law.
Of Relevance: An Overview of Data Protection Regulation in the United States. As you can see, specific industries and situations may be regulated by other laws, including HIPAA, FTC Act,COPPA, GLB Act, FINRA or others.
Disclaimer: We are not lawyers nor legal experts, any and all information contained in this post should not be taken as legal advice – please consult with a lawyer regarding any legal matters pertaining to data breaches or other issues.



