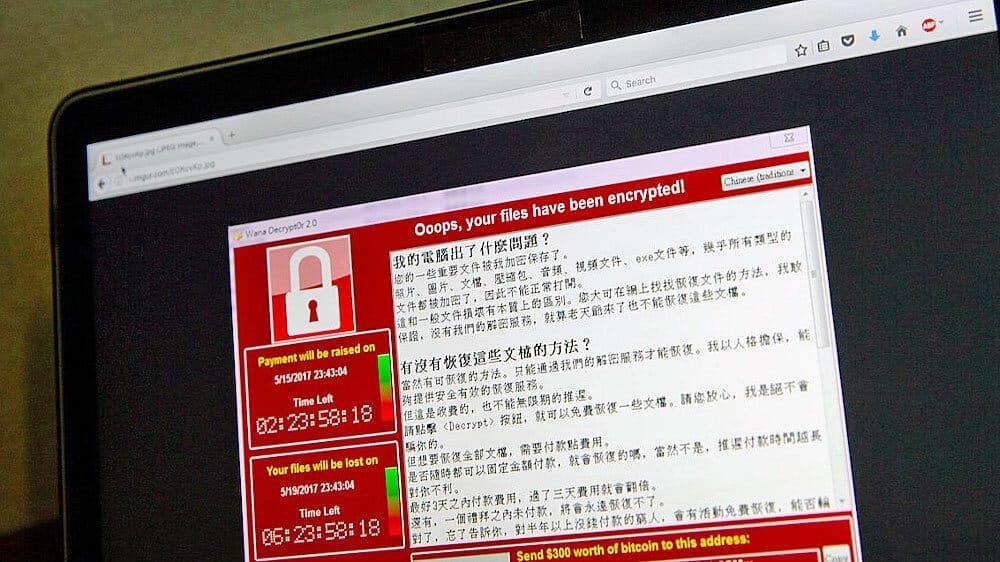
Although expected to produce more hassles for IT admins this Monday, the dust has mostly settled on this past weekend’s now-famous WannaCry ransomware attack. This program, targeting Windows XP, Windows Server 2003 and other legacy versions of Microsoft Windows, infected more than 230,000 computers in 150 countries, encrypting user data and demanding a bitcoin ransom for its return.
While the attack spread by phishing emails, it also infected exposed systems through networks without a Windows XP/Windows Server 2003 security patch issued by Microsoft on March 14th, 2017. Though much of the attack was stopped by an apparent killswitch found by a 22-year-old British researcher, and while a second one has also been found, versions of the ransomware have again emerged without these apparent killswitches.
#Wannacry want to actually cry? Media frenzy over issue that has cost the world under $50,000 so far…
— Mike Petsalis (@mikepetsalis) May 15, 2017
If you’re concerned about how to respond to this or prevent other such ransomware attacks from harming your organization, take the following steps to restore confidence in your networks:
Step 1: Update your Windows patches and enable Windows Auto-Updates
Update to the latest patches available for Windows (and be sure to not defer future updates to more convenient times). Also, be sure that auto-updates are enabled on workstations throughout your organization and take time to immediately run updates in the wake of WannaCry.
For all modern versions of windows, find links to all necessary patches here.
For Windows XP, find the necessary patches here.
For Windows 2003, necessary patches can be found here.
Step 2: Update and enable auto-updates for your desktop AntiVirus software
While desktop anti-virus is the last line of defense against threats like this, updating it and keeping it updated will prevent a clear majority of threats like the WannaCry ransomware from infiltrating your network’s workstations and locking out user data. WannaCry threats via email are typically blocked by email-level antivirus, while external links to a downloader require URL defense in order to prevent cryptolocker style infections like WannaCry.
Step 3: Get Colleagues to be extra-paranoid of any attachments for the next week (or until the dust settles)
All members of your organization should know from where and for what purpose they are receiving email attachments. If they receive an email with an attachment from even a recognizable source, they should call to check and ensure that they’ve been sent that email and attachment from that colleague or business partner, ensuring it has not come from a masked or malicious actor.
Step 4: Exercise extreme caution in browsing following attacks like WannaCry Ransomware
Outside of personal internet connections, employees should be advised against performing their everyday surfing at the office. In the wake of a major attack like this one, even sites like Microsoft’s can be at risk of spreading malware, so exercising extreme caution during periods like this is crucial if certain online activities are not 100% required.
While no one can guarantee 100% safety from malware waves like this one, effective Antivirus tools mixed with email, web and protection from peer-to-peer network dangers can give organizations confidence. What’s more, as an IT or system administrator, an effective response to cyberattacks like this one, even in cases like WannaCry where there’s “more smoke than fire”, can prove your value to your team and give them confidence in following your advice online.
For a more complete guide on how to prevent any ill effects from ransomware attacks like WannaCry, check out this article by Help Net Security to understand the full spectrum of urgent and less-urgent changes you can make to protect your networks. We also released a white paper on trends on cybersecurity where we identified the importance of ransomware protection. You can download it here.
If you are a Vircom customer and you are concerned about WannaCry, please reach out to our support team with any questions or concerns. If you are looking for comprehensive email protection with obsessive customer support, contact us to find the solution that’s right for you.