Understanding Email Fraud
RISKS
Shield your Business from Email Fraud
This cunning strategy deceives employees into revealing sensitive information like account numbers or initiating
unauthorized financial transfers.
Stay alert for suspicious emails, phishing email and phishing attacks, which could be potential attempts at identity theft or manipulative social engineering tactics.
The adoption of robust email authentication is vital in our cybersecurity plan, preserving the integrity of your digital identity against cyber risks.

CEO FRAUD ATTACK
$43B+
Economic Impact
Source: FBI
BEC Global Reach
177 Countries
BEC scams have been reported in all 50 US states and 177 countries.
Source: FBI
SMBs are a HOTSPOT for Cyber Attacks
Recognizing CEO Impersonation Threats
Recognizing these threats requires vigilance and awareness of the common tactics used by these cybercriminals.
Proactive Measures to Counter Email Fraud
Taking proactive measures to counter email scams, a prevalent type of scam, can help protect your organization’s financial stability, reputation, and sensitive data.
This includes implementing robust email protection measures such as email authentication, and educating employees about the risks of suspicious emails that may lead to identity theft. It’s crucial to instill a culture of suspicion towards any unusual email activity.
- Verifying email URLs align with business names
- Looking out for misspelled hyperlinks.
- Avoid sharing login details or PII via email
- Confirming sender's email addresses, particularly on mobile.
- Enabling full email extension view on staff PCs
- Regularly monitoring financial accounts for discrepancies.
Effective Email Fraud Protection
Advanced Techniques for Email Hoax Identification

Building a Resilient Email Fraud Defense System
ROBUST PROTECTION BUNDLES
Protect your business
with Vircom's comprehensive security bundles.
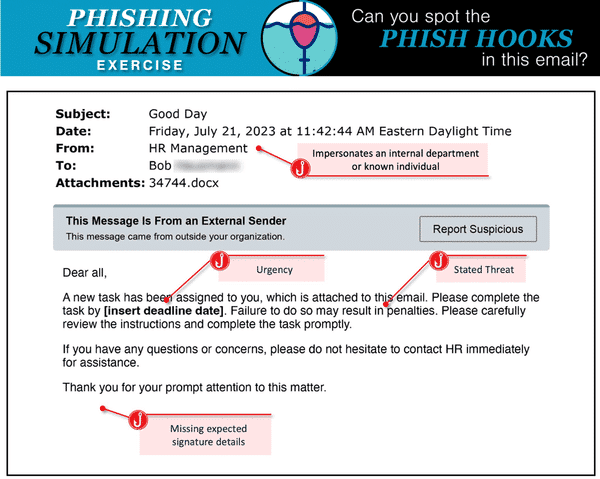
Analyzing a Scam Email Example
Deconstructing an Impersonation Email
These emails often appear to come from the head of the organization or another senior authority.
They usually contain requests for sensitive information or financial transactions, creating a false sense of urgency to manipulate the recipient into compliance.
Scammers employ a multitude of common tricks to make their deceptive emails seem legitimate:
- Spoofed email addresses: They mask the sender's address to make it look like it's coming from a trusted source.
- Urgent Requests: They create a sense of urgency, pressuring the recipient to act quickly without thinking.
- Request for Sensitive Information: They solicit personal information, such as passwords or credit card numbers.
- Links to Fake Websites: They include links to counterfeit websites designed to look like authentic ones.
- Attachments with Malware: They attach files that contain malicious software designed to compromise the recipient's system upon download.
Key Takeaways for Email Safety
The cornerstone of robust email security is awareness.
Regular training sessions to educate employees about the latest threats, vigilant surveillance of incoming communications, and the deployment of sophisticated threat recognition tools can all dramatically diminish the risk of falling prey to these impersonation schemes.
Proactive prevention is always more effective than reactive measures.
By equipping your workforce with the right knowledge and tools, you can create a strong line of defense against sophisticated email attacks.

Preventing Email Fraud Impact
Limiting Your Exposure to Fraud
Adopt rigorous security protocols, keep systems up-to-date, and empower your employees with customized trainings and simulations specifically designed to identify sophisticated digital threats.
Relying Solely on Users Can Be Risky
Trusting users entirely for email safety is risky; one error can lead to substantial losses. However, Proofpoint Essentials Advanced Threat Protection provides built-in email fraud protection, filtering out spam, spoofed emails and harmful content, ensuring user safety.
Taking Action to Stop Fraud
The Importance of Email Protection
Investing in email scam protection is not just about preventing financial losses. It's a foundational element that can make or break your organization's reputation and protect sensitive data from falling into the wrong hands. It ensures the smooth running of your business but also fosters a sense of trust and reliability among your clients and stakeholders.
Benefits of a Secure Email Gateway
A secure email gateway can proactively detect and block malicious emails before they reach your users' inboxes. This not only protects your users but also reduces the risk of data breaches.
“Vircom’s solutions are an integral component of our cybersecurity defense. Their continued product enhancements and overall effectiveness combined with staff sense of urgency and follow up are one of the reasons Vircom is one of our longest running partners.”
Protect your organization from sophisticated email threats and fraudulent activities.

