Shield Against Ransomware
Strengthen Your Defense Against Ransomware Attacks
Ransomware is one of the most damaging cyber threats, with 75% of attacks starting from phishing emails. Office 365 phishing attacks often use sophisticated tactics to breach organizations and steal sensitive data.
The best strategies to mitigate ransomware risks include adopting a multi-layered strategy: fortifying security, educate users, and maintain a robust IT infrastructure. Regular system hardening and updates are key to reducing vulnerabilities.
While no single solution can fully prevent ransomware, proactive measures significantly lower the risk.

$200,000 USD was the median ransom payment in Q4 2023
Understanding Ransomware
and Its Impact
Ransomware, a type of malicious software, encrypts your data, holding it hostage until a ransom is paid. This cybersecurity threat can infect your network through various means, including phishing emails, malicious attachments, and exploiting security vulnerabilities.
A successful ransomware attack can lead to data loss, financial costs, and severe reputational damage.
The sophistication and frequency of these attacks are growing, making it crucial to understand every facet of the threat to mitigate risk and manage the fallout of an incident.
Vircom’s advanced ransomware protection solutions offer comprehensive defense mechanisms tailored to protect your organization against the ever-present threat of ransomware, to NOT pay the ransom or disclose sensitive data.

Ransomware: The Real Costs and Consequences
IT Downtime Cost
$5,600 /min
Ransomware Email Threats
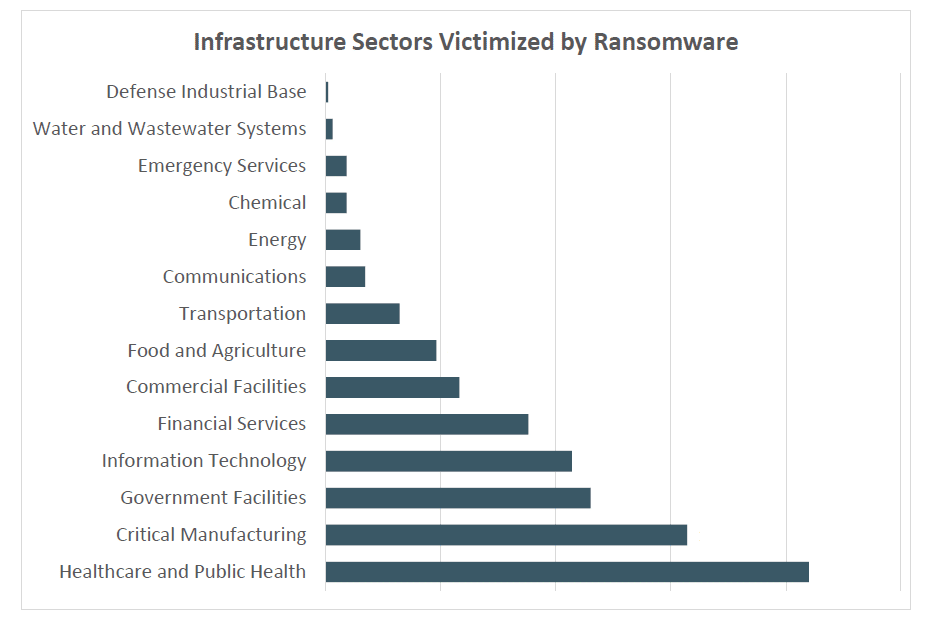
Ransomware and Phishing: A Dangerous Combination
Ransomware Protection Strategies
Ransomware Prevention
Best Practices
Endpoint protection
For robust ransomware defense, deploy an Endpoint protection platform (EPP). They serve as a first line of defense by securing the various entry points for potential ransomware attacks, such as desktops, laptops, and mobile devices. These platforms typically combine antivirus, antispyware, firewall, and other security components to prevent malware from infecting endpoints.
Backup Solutions
The single most important thing that organizations can do in their ransomware prevention strategy is to ensure that they have good backups.
- Backup Often
- Keep Backups Offsite
- Test your Backups
Recovery Solutions
Recovery solutions serve as a safety net, allowing quick restoration of operations and data with minimal disruption. Key components of recovery solutions include:
- Data backup and restoration
- Disaster recovery planning
- Cloud recovery services
- Zero trust architecture for recovery processes
Update and Patch
While Email Phishing is consistently a top attack vector for ransomware, RDP Compromise and Software Vulnerabilities are the other more common attack vectors. Having a regular patch schedule can ensure that you are protected from the latter two. Make sure to keep all operating systems, security software, applications, and network hardware regularly patched and up to date. This is especially important for any public internet-facing devices.
User Awareness Training
Implementing user training and phishing exercises is one of the four ways to prevent ransomware recommended by the IC3 Raising users’ awareness about potentially harmful links and attachments are important steps to preventing ransomware and phishing.
Educational Resources
and Best Practices
Learn more about ransomware and how to protect your organization with Vircom’s educational resources. We provide best practices, ransomware protection strategies, and proactive tips to help you and your team stay informed and prepared.
Tips for Ransomware Defense
Multifactor Authentication (MFA)
A large factor in how damaging a successful ransomware intrusion becomes is what level of access the compromised account has. While larger organizations will implement a Zero Trust architecture, smaller organizations should, at a minimum, enforce Multi-Factor Authentication for all users and limit access to key systems and data.
Cyber Insurance
There’s no way to avoid ransomware attacks entirely which is why you need to also be prepared to solve ransomware infections. Part of that solution is having adequate liability coverage. Having adequate coverage helps mitigate the financial impact of a successful ransomware attack.
Incident Response
Having an incident response plan and a business continuity plan that is written down and reviewed periodically ensures that when the worst happens your team is prepared to react. Being locked out of critical systems is a stressful situation but following ransomware best practices for prevention and response and knowing in advance how to respond will lead to better outcomes. Every response plan is different, but it usually includes isolating the infection as quickly as possible, contacting law enforcement, and recovering from backup.
Avoid the Devastating Impact of Ransomware
Ransomware Proactive Prevention Solutions
While there’s no single ransomware solution, a layered security approach along with following best practices for prevention can help stop ransomware attacks before they gain a foothold in the organization.
Vircom’s ransomware protection strategies are designed to stop ransomware in its tracks. By combining advanced threat detection, endpoint protection, and malware defense mechanisms, our solutions offer robust protection against ransomware and other types of malware.
Ransomware Solutions by Vircom
Anti-malware and Anti-spam
Ransomware attacks often leverage known compromised infrastructure or virus signatures. Our anti-malware and anti-spam technology will block the large volume of threats that come from known threat actors.
Spoofing Protection
Anti-spoofing policies leverage email authentication protocols (SPF, DKIM, DMARC) to block exact domain spoofing which is often used to trick a user into an action that would infect them with ransomware. By blocking brand impersonation in emails and attachments, we protect users from ransomware threats.
URL inspection and time-of-click checks
We leverage big data techniques to build statistical models to provide predictive analysis of URLs even before a click. URL rewriting lets us provide real-time analysis at time-of-click to ensure that the destination hasn’t been redirected to a malware-hosting location.
Attachment analysis including sandboxing and behavioral scans
Attachment analysis is a key layer of ransomware protection, scanning email attachments for malicious content before they reach the user's inbox. This includes sandboxing to isolate and test suspicious files, and behavioral scans to detect harmful patterns. By blocking malicious files, attachment analysis keeps your devices and network safe from ransomware.
Security awareness training
Phishing emails often deliver ransomware by tricking users into clicking malicious links or attachments. Phishing simulations test users' ability to recognize and report these threats, providing immediate feedback and guidance. Ongoing user awareness training educates users on spotting fake sender addresses, avoiding suspicious attachments, and verifying URLs. These measures reduce human error and enhance organizational resilience against ransomware.
Continuity solutions
Email continuity solutions allow end users to continue to work even when the infrastructure is offline. The Emergency Inbox is immediately accessible to users when email is being deferred.
Office 365 monitoring
Continuous monitoring of Office 365 accounts will automatically flag suspicious user and account behavior to detect attack attempts, compromised accounts, and malicious activity.
How to Stop Ransomware in Its Tracks
How to prevent ransomware is really a question of how to be best prepared for ransomware.
Office 365 Ransomware Protection
The Coalition Cyber Claims Report reveals Office 365 users are twice as likely to file cyber insurance claims compared to Google Workspace users, largely because most Office 365 plans don’t include Defender, exposing them to impersonation attacks and malicious URLs.
Monitoring of compromised Office 365 accounts and quick remediation thereof is also quickly becoming an important part of any strong defensive plan.
Vircom provides crucial Account Take Over (ATO) monitoring and alerting, identifying unauthorized access and issuing quick alerts to prevent breaches and ransomware attacks.
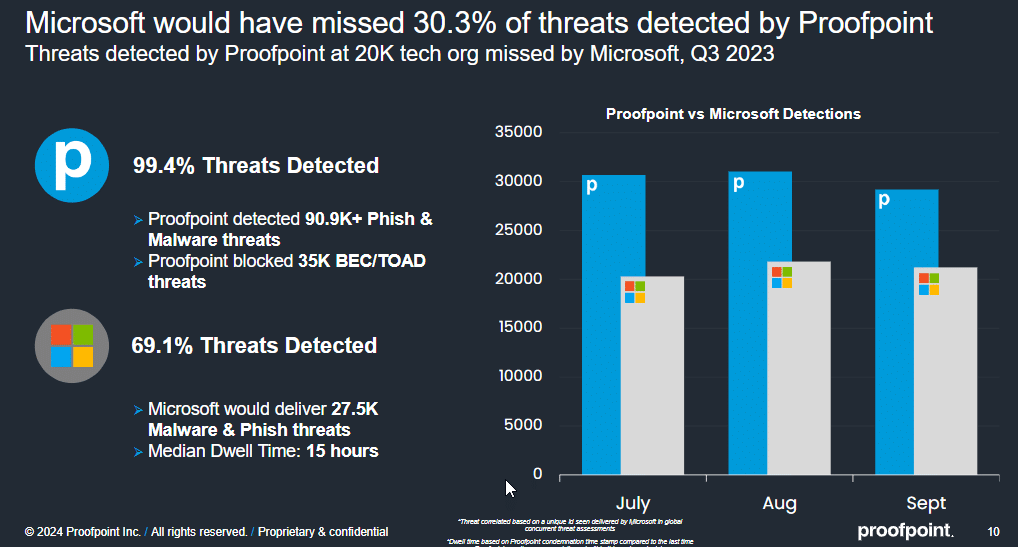
Preventing Ransomware Attacks and Phishing Scams
Phishing scams are the main attack vector for ransomware and so, of course, a key aspect of ransomware prevention is phishing prevention.
Not all email security systems are equal. It’s important to leverage a solution that uses AI and machine learning, performs both link and attachment sandboxing, and can detect various forms of spoofing.

Protect your organization and clients with Vircom's Advanced Ransomware Defense

